Use Gingr Pet Business Software for Pawesome Results
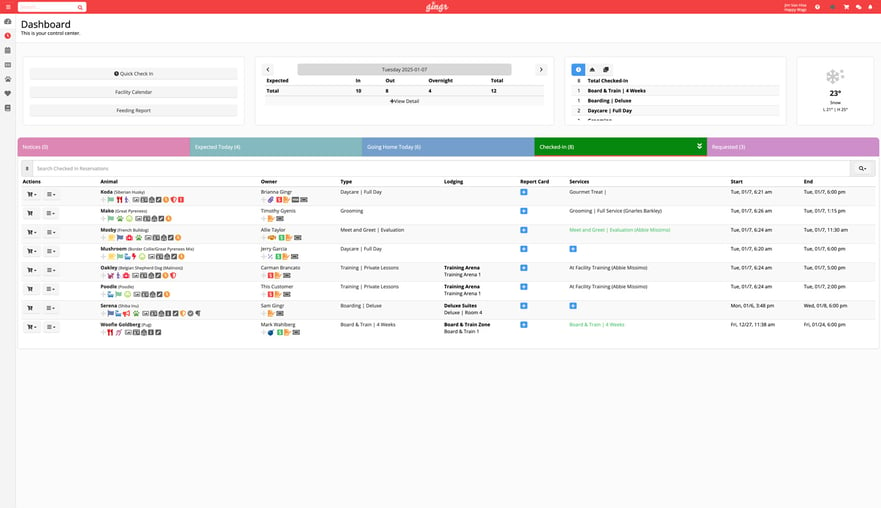

Benefits for Pet Business Owners
Maximize Revenue
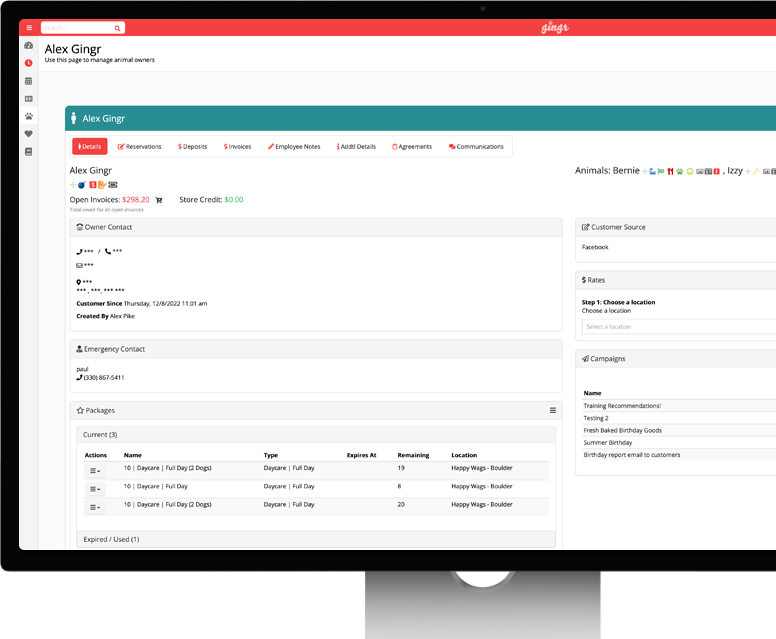
Optimize Operations
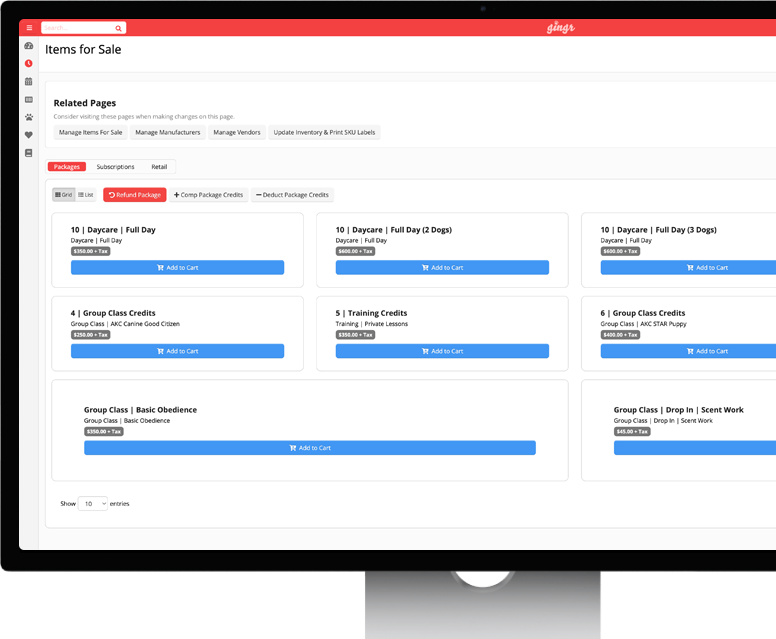
Build Customers for Life
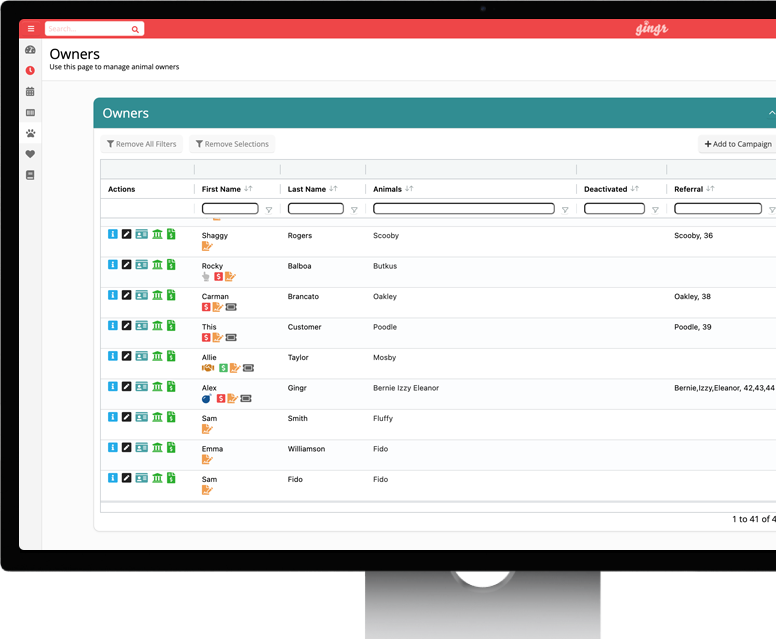



Features That Help You Grow
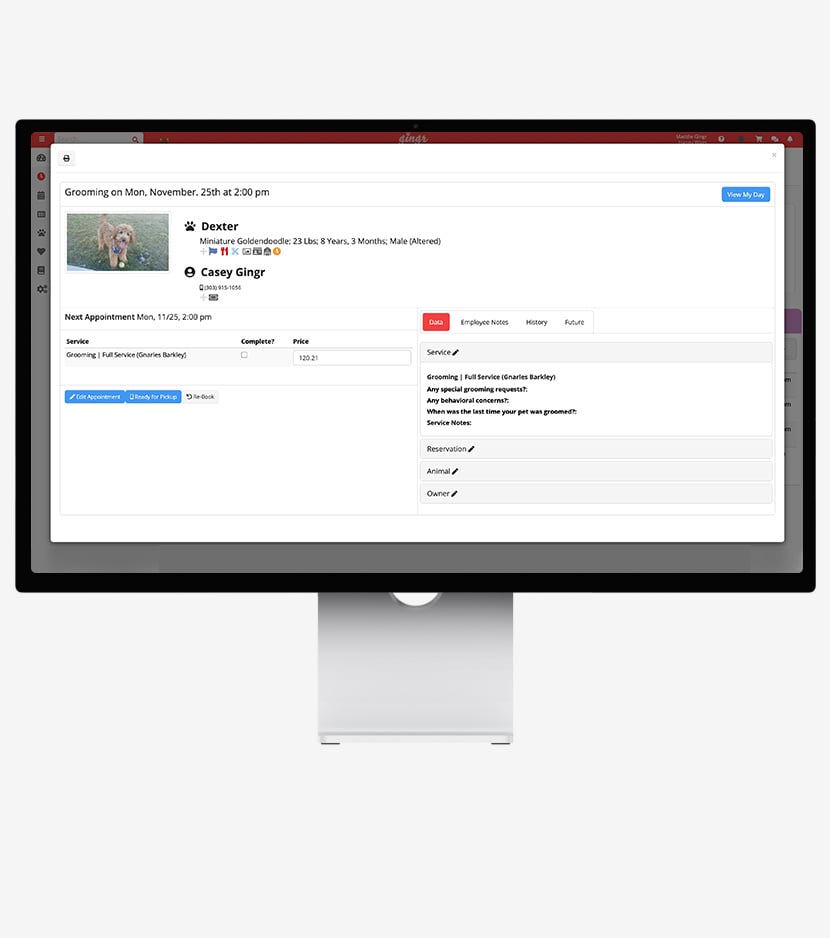
Pet Scheduling Software
Effortlessly manage pet daycare, boarding, grooming and more from intuitive drag-and-drop calendars. Each pet comes with their own appointment card with all the details you need.
- Book appointments
- Pay invoices
- Receive reminders and notifications
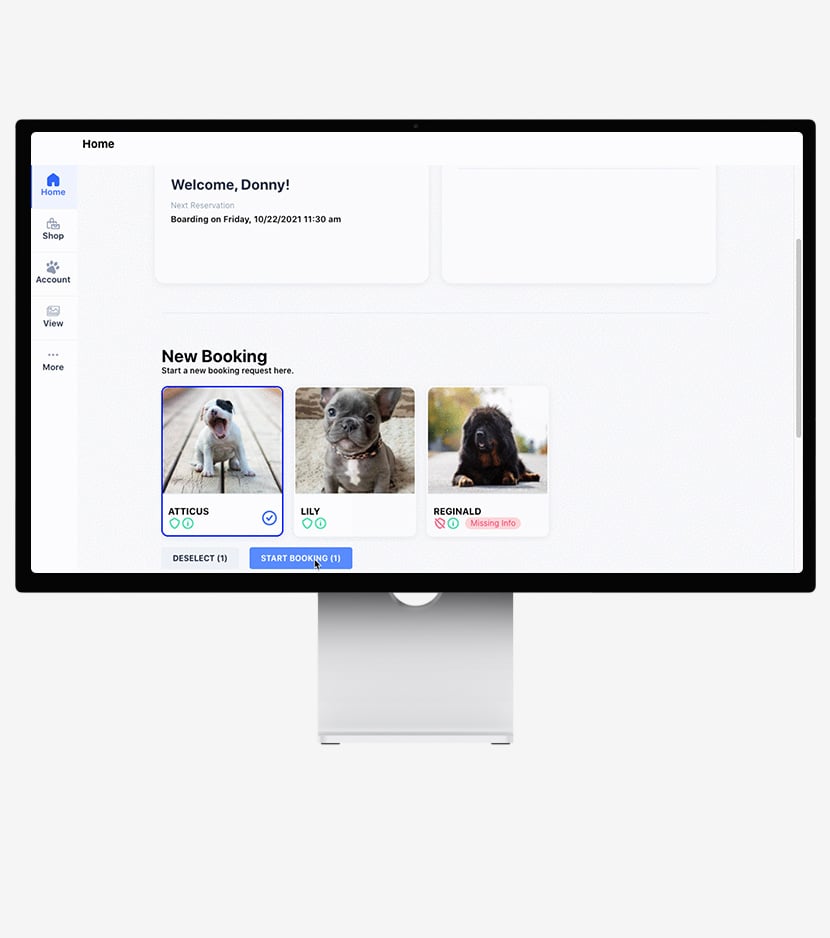
Pet Parent Mobile App
Who doesn’t rely on their phone to manage their lives these days? Give your customers the power to book and keep track of appointments with ease.
- Book appointments
- Pay invoices
- Receive reminders and notifications
.png)
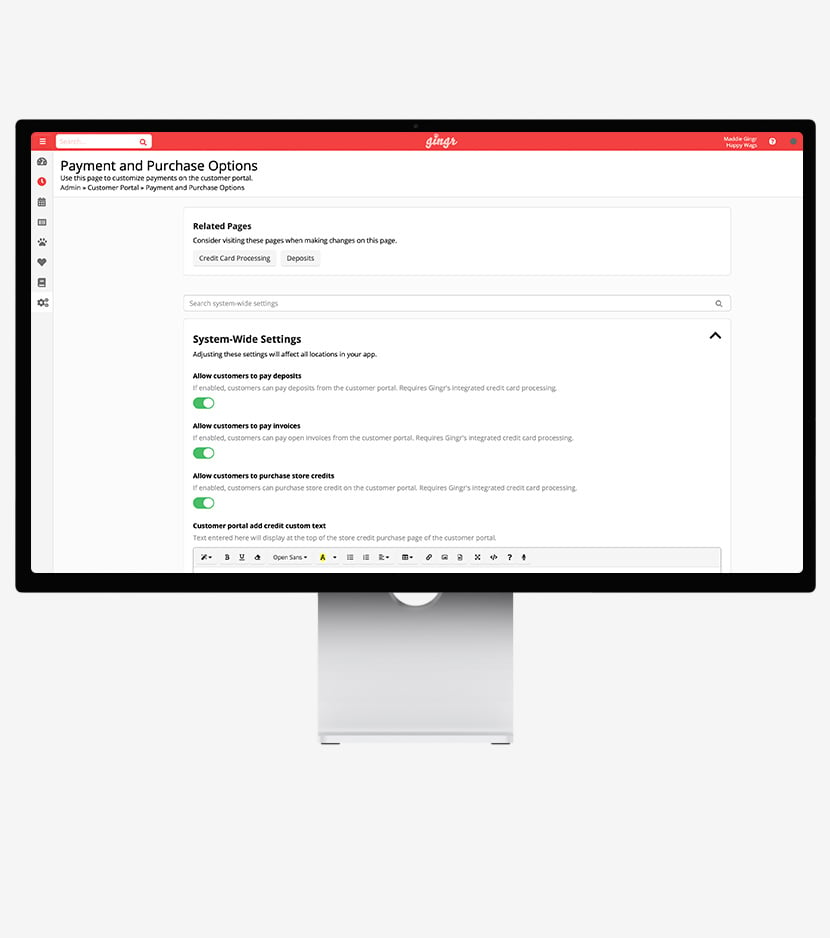
Integrated Payment Processing
Secure, seamless payments keep things moving. Automated pricing rules and invoicing ensure you get paid the right amount for every reservation. No time-consuming math equations required!
- Secure mobile payment collection
- Cash drawer & receipt printer integration
- Faster transactions
Gingr PreCheck
Reduce waiting-room chaos with faster check-ins. Similar to checking in before a flight, pet parents complete a detailed check-in form in advance to free up your staff’s time.
- Online, self-serve portal
- Curbside check-in
- Automatic “I’m here!” notifications
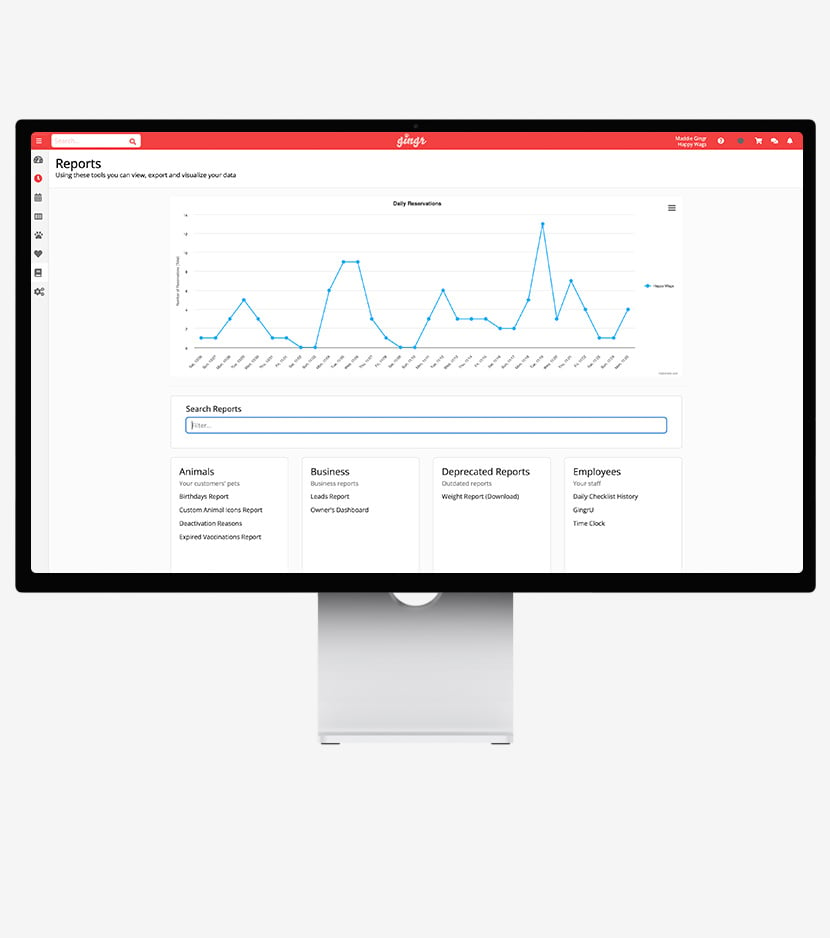
Business Analytics
Make informed decisions with detailed reports and insights that equip you with the tools you need to oversee your business like the pros.
- Period-by-period comparative reports
- Multi-location data in one place
- Booking source insights

.png)





